With PowerShell V3 Microsoft provides us with Two ways to delegate administration.
- Session Configuration Files – It allows us to define a endpoint on a machine which exposes only the cmdlets and modules which we want, it can be configured by configuring a .psd1 file.
- RunAS – It allows to configure a session configuration and specify which set of credentials should be used in that session configuration.
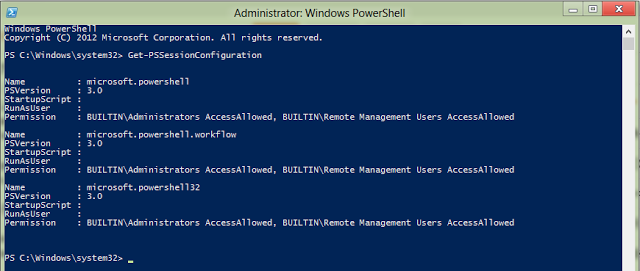
First let us list out the List of all PSSession Confgurations which exists on our server, we can do so by using
Get-PSSessionConfiguration.
The Get-PSSessionConfiguration cmdlet gets the session configurations that have been registered on the local computer. This cmdlet is used by system administrators to manage customized session configurations for their users.
Beginning in Windows PowerShell 3.0, you can define the properties of a session configuration by using a session configuration (.pssc) file. This feature lets you create customized and restricted sessions.
So if i do a Get-PSSessionConfiguration i get the list of all PSSession Configurations existing on my local system.
When ever we use Remote Session cmdlets its uses microsoft.powershell session configuration by default, its restricted only for administrators to connect to it.
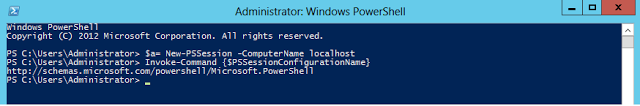
So if i create a new ps session to my local host i can see which PSSessionConfiguration im using
PS C:Windowssystem32> $a= New-PSSession -ComputerName localhost
PS C:Windowssystem32> Invoke-Command {$PSSessionConfigurationName}
So above i can see that im connected to Microsoft.PowerShell session configuration
Now to allow team specific administration levels i need to create a new pssession configuration.
So as discussed lets create now three of them for storage, exchange and network team, also please do note none of the members of the groups or the group itself is a part of administrators group on the server. Hence we are delegating the permissions.
Next i can set these session configurations to run commands with administrator credential.
Now we would create a session configurations files to restrict powershell access as per team requirements.
We would be using New-PSSessionConfigurationFile cmdlet and specify the path where the session configuration files needs to be created, also specify the modules which needs to be imported also specify the cmdlets which needs to be visible and the session type to be used to have an interactive remote session with the server.
So let me show you an example for our Networking Team First.
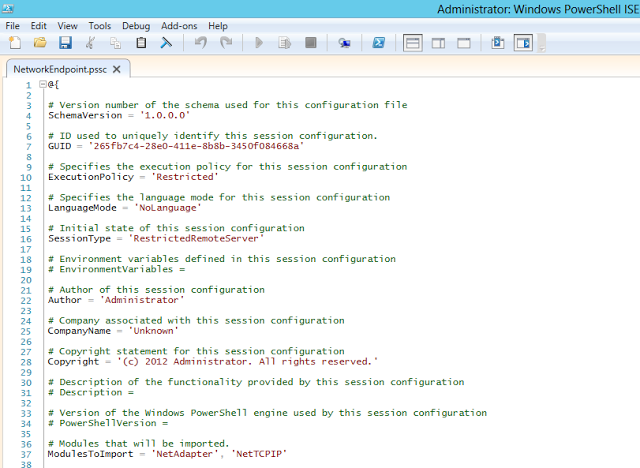
Below im using the New-PSSessionConfigurationFile cmdlet to create a session configuration file to expose only the required modules of NetAdapter and NetTCPIP to be used only by the Networking Team, im naming the session file as “NetworkEndpoint.pssc”
PS C:Windowssystem32> New-PSSessionConfigurationFile -Path c:2012vmsNetworkEndpoint.pssc -ModulesToImport NetAdapter,NetTCPIP -SessionType RestrictedRemoteServer
Now if i go and manually check on whats present inside that .pssc file i can see that it contains a hashtable which contains that information
Now i will go ahead and create the PSSessionConfiguration and point it to session configurationfile using Register-PSSessionConfiguration.
So let me now create it for Networking Team.
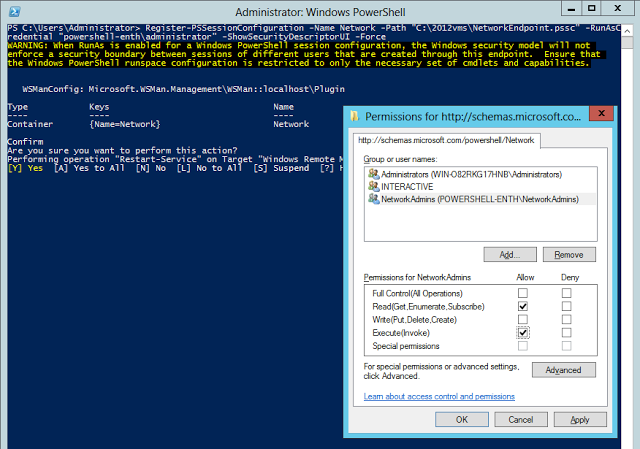
PS C:Windowssystem32> Register-PSSessionConfiguration -Name Network -Path "C:2012vmsNetworkEndpoint.pssc" -RunAsCredential "powershell-enthadministrator" -ShowSecurityDescriptorUI -Force
Once i assign the required permissions (execute) to the networkadmins they would be running the commands for NetAdapter and NetTCPIP modules under context of powershell-enthadministrator who is the administrator for the server.
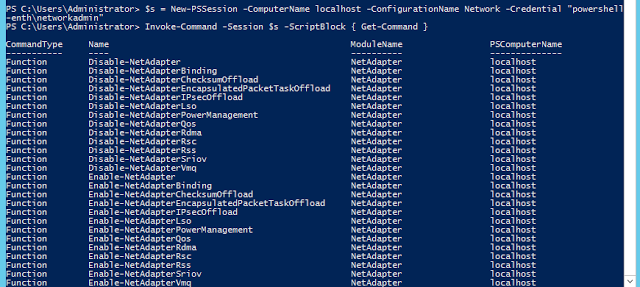
Now if i again connect as NetworkAdmin who is a part of NetworkAdmins group using the Networkendpoint, im able to see that i have a restricted set of cmdlets to use which are all related only to networking.
PS C:Windowssystem32> $s = New-PSSession -ComputerName localhost -ConfigurationName Network -Credential "powershell-enthnetworkadmin"
PS C:Windowssystem32> Invoke-Command -Session $s -ScriptBlock { Get-Command }
Similarly we can create delegate cmdlet permissions to admins based on their team type and keep them restricted only to cmdlets dealing with their technology expertise.